Cyber Laws and Trends: How the Internet Just Became a Crime Scene


Author and SIA member Steve Surfaro
If you’re like me, your “typical” cybersecurity report on what’s trending starts with a comparison of market studies reporting on what’s happened and projections of what sector will experience which exploits. The first half of 2018 is anything but typical, with local and global government about to pass far-reaching legislation and our “internet crime scenes” already having over 53,000 incidents and 2,216 confirmed data breaches this year.
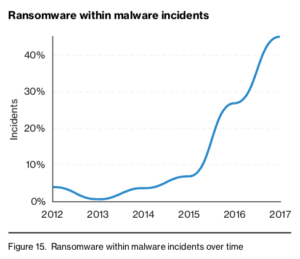 We’ll get into the “cyberlaw,” but first, a worthy mention in the trends report category is the recent release of the 11th edition of Verizon’s Data Breach Investigations Report: 48 percent of breaches featured hacking, 30 percent included malware, 50 percent were carried out by organized criminal groups and 12 percent involved actors identified as nation state- or state-affiliated. Within the malware category, ransomware accelerated to over 40 percent of all malware incidents over time. No surprise here: ransomware has little to no risk or cost to the actor(s) involved, can command larger ransoms as deployed easily across entire organizations and many devices and can succeed with no reliance on monetizing stolen data – they get your money upfront! Clearly ransomware requires its own post.
We’ll get into the “cyberlaw,” but first, a worthy mention in the trends report category is the recent release of the 11th edition of Verizon’s Data Breach Investigations Report: 48 percent of breaches featured hacking, 30 percent included malware, 50 percent were carried out by organized criminal groups and 12 percent involved actors identified as nation state- or state-affiliated. Within the malware category, ransomware accelerated to over 40 percent of all malware incidents over time. No surprise here: ransomware has little to no risk or cost to the actor(s) involved, can command larger ransoms as deployed easily across entire organizations and many devices and can succeed with no reliance on monetizing stolen data – they get your money upfront! Clearly ransomware requires its own post.
Overnight cybersecurity
Facebook CEO Mark Zuckerberg delivered 10 hours of congressional testimony in just two days, taking nearly 600 questions on Capitol Hill and giving a rare window into some of the most controversial issues online.
"We need comprehensive privacy and data security legislation," said Rep. Frank Pallone Jr. (D-N.J.), the House Committee on Energy and Commerce’s ranking member. "We need baseline protections that stretch from internet service providers to data brokers to app developers and to anyone else who makes a living off our data."
Although support for new privacy laws is evident, Zuckerberg refused to endorse the idea, saying only that he supported greater privacy protections in theory.
The General Data Protection Regulation (GDPR) will go into effect on May 25; this regulation will require internet firms to be more transparent about their data policies and give users more control over their own information. GDPR will only apply to European countries, but privacy advocates have been urging Facebook to extend the changes that will be required to rest of the world.
Federal, state and global cyber law making in the last several months already has many industry professionals reaching their own verdicts and installing safeguards.
Federal
S.2639 - CONSENT Act
- May be cited as the “Customer Online Notification for Stopping Edge-provider Network Transgressions” or the “CONSENT Act”Requires the Federal Trade Commission to establish privacy protections for customers of online edge providers that provide edge services
- An edge service is delivered through a software program, including a mobile application, or over the internet, directly or indirectly, through a connected device
- Special note: this bill was introduced at the time of Mr. Zuckerberg’s (Facebook) testimony but could affect any cloud-based software solution
- Status: Introduced in Senate (April 10, 2018)
- Opinion: Medium industry impact
S.1691 - Internet of Things (IoT) Cybersecurity Improvement Act of 2017
- Disclose any hardware, software or firmware component with any known security vulnerabilities or defects
- Sets standards for federal vendors providing broad spectrum of business interests, from consumer electronics to the oil and gas sector
- Provides for some method of authenticity protection, such as a digital signature, so that unauthorized updates can be automatically detected and rejected
- Regarding vulnerabilities, requires notification, updates, timely repair and continuation of services
- Status: Introduced in Senate (Aug. 1, 2017)
- Opinion: High industry impact
H.R. 3202: Cyber Vulnerability Disclosure Reporting Act
- Requires the U.S. secretary of homeland security to annually report on policies and procedures developed for coordinating cyber vulnerability disclosures, in accordance with section 227(m) of the Homeland Security Act of 2002
- Nationwide notification by solution providers that own or possess data in electronic form containing personal information, following the discovery of a breach of security of the system
- Status: Introduced in House (Nov. 30, 2017); not expected to pass
- Opinion: Medium industry impact
National Institute of Standards and Technology Draft Report on Executive Order 13800
- In response to Executive Order 13800, Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure (the order directed the secretary of commerce, together with the secretary of homeland security, to “lead an open and transparent process to identify and promote action by appropriate stakeholders” with the goal of “dramatically reducing threats perpetrated by automated and distributed attacks" (e.g., botnets
- More of a set of best practices for federal agencies to mitigate threats to the Homeland Security Enterprise,with the hope that industry stakeholders will adopt these practices once the safeguards are established
- Status: Complete
- Opinion: Low industry impact
H.R.3359 - Cybersecurity and Infrastructure Security Agency Act of 2017
- Reorganizes the U.S. Department of Homeland Security’s National Protection and Programs Directorate (NPPD), the office responsible for protecting the nation’s vital industries from both online and physical attacks
- Would rename NPPD as the Cybersecurity and Infrastructure Security Agency
- Status: Introduced in House (July 24, 2017)
- Opinion: Low industry impact
S.2261 - Secure Elections Act
- Aims to protect the administration of federal elections against cybersecurity threats
- Status: Introduced in House (Dec. 21, 2017)
- Opinion: Low industry impact
States
SB 315 Georgia Computer Crime Bill
- Would establish a “misdemeanor of a high and aggravated nature" for persons who gain "unauthorized" access to a computer or computer network, with a maximum $5,000 fine and yearlong jail sentence
- Specifically defines unauthorized computer access as "any person who intentionally accesses a computer or computer network with knowledge that such access is without authority shall be guilty of the crime of unauthorized computer access," a misdemeanor of high and aggravated assault
- Status: Passed
- Opinion: High industry impact
Oregon Cybersecurity Advisory Council
- Established under Senate Bill 90, signed by Governor Kate Brown on Sept. 19, 2017, to develop a shared vision for the establishment of a cross-sector Cybersecurity Center of Excellence, in collaboration with Oregon’s cyber-related industries, private sector security practitioners, educational institutions, law enforcement and local governments
- Status: Passed
- Opinion: Low industry impact
With the state of Georgia’s cybersecurity bill passing, the impact on much needed cyber research and penetration testing can be devastating. Most vulnerabilities are discovered by individuals involved in “white hat” or “gray hat” network testing that could be misinterpreted as intentional cybersecurity breaches. With the growing use of artificial intelligence (AI) to execute “playbooks” to respond to malware attacks, the need to “seed” the AI with improved identification and processes is essential. Today’s advanced endpoint security solutions improve network security by mining IP addresses of malicious social media posters and extracting patterns and communications artifacts. These form the network security “playbooks,” executed more rapidly by AI than humans can.
Although focused on cyber privacy, the Electronic Frontier Foundation –a nonprofit organization defending digital privacy, free speech, and innovation – is a useful resource. The link to cyberlaw progress is here. Another site, CSOonline, is a cyber news accumulator where trends and the effects of cyber regulation are reported.
The views and opinions expressed in guest posts and/or profiles are those of the authors or sources and do not necessarily reflect the official policy or position of the Security Industry Association (SIA).
