The Potential of Generative Artificial Intelligence to Revolutionize Physical Security

Solutions are not just hype; they can reduce risk and improve productivity

Artificial intelligence (AI) is defined as the ability of a computer or other machine to perform tasks that are normally thought to require human intelligence. This description fits many of the automated security system features that have been on the market for many decades, so it is natural to wonder how AI suddenly became so newsworthy and a top agenda item in every security and related technology discussion.
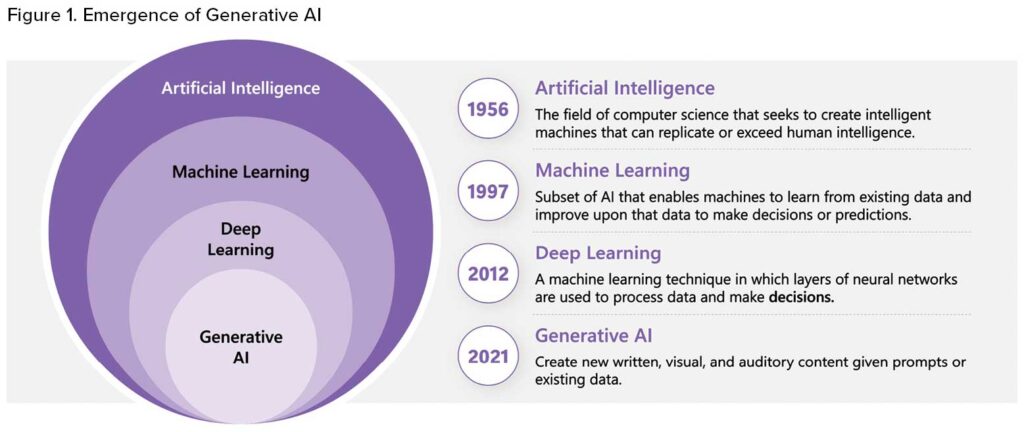
A paradigm shift started a few years ago with the emergence of “generative AI” (gen-AI) systems that generate various forms of novel output, including text, code, graphics or audio (Figure 1). Examples of this type of system include generative pretrained transformer (GPT) chatbots and text-to-image generators, which can be tailored to specific areas, tasks or personas. These most recent advancements have signaled the dawn of a new era of potential.
The Future Is Now
Gen-AI will revolutionize physical security in two foundational ways. The first is the manner in which users interact with systems, which will be transformed by more knowledgeable virtual assistants possessing a holistic understanding of the security program and the ability to learn continuously. Security system operators and managers will be able to leverage natural language queries into integrated technology systems and obtain results that historically took far more time and resources to produce. Officers who might ordinarily need to reference an exhaustive catalog of operating procedures, post orders, logs and site-specific documentation will be able to efficiently leverage a common tool via mobile or desktop device that quickly transforms typed or spoken prompts into actionable feedback. Benefits should be most visible for newer and less experienced staff, as well as during emergencies, when the performance of people is notoriously less consistent because of time pressures and stress.
Modern AI modules embedded into operational communication systems will enable real-time engagement with company employees, visitors and vendors. Tasks that might have traditionally required face-to-face interaction with onsite security will be addressed by a straightforward tool that contains encyclopedic knowledge of the most current references securely in its dedicated model repository. Questions about security policy, work rules, access management, permissions, escorts and security systems can be quickly and consistently addressed in a way that will be easier for users to understand.
These tools can support onboarding and ongoing security awareness by addressing both common and complex queries on everyday issues that would have previously required escalation or direct engagement with more experienced team members. Improved customer satisfaction will naturally result from the time, energy and cost savings associated with more efficient and effective interactions with security.
The second fundamental transformation will be tied to new capabilities that security systems and devices will have to perform tasks and identify issues that have eluded technology to date. Systems outfitted with enhanced reference models including current internal/external threats, risks, policies, procedures, system health, and other historical operations data will have the ability to identify emerging risks, trends, suspicious activity, security violations and other issues of potential concern that may not have been discovered until an attack or device/system failure had already occurred.
The Rise of Computer Vision
Whether referred to as video analytics, camera cognition or computer vision, this tool will be able to achieve real-time processing of video data that can uncover complex security and safety issues. Individual devices will have embedded AI modules that can perform advanced analytics at the edge that previously demanded centralized, expensive and resource-intensive systems.
AI solutions based on machine learning modules will be applied to visual input from cameras both in real time and on demand. Breakthrough experiences will include modules that learn to analyze video images based on current work rules, task-specific activities, and expected operations with historical context. Alerts can be triggered when variations from the established parameters are observed, giving onsite security timely and actionable intelligence they can use to assess the urgency of an incident and respond accordingly. Examples of situations in which this could be valuable include critical equipment being accessed without a valid work order, movement of assets outside the secure path of travel within a facility, safety violations that historically have led to security incidents, identification and tracking of drone incursions and the taking of pictures/video of critical assets without prior authorization.
Virtual video escorts will free up valuable officer resources by ensuring that security policies (e.g., two-person rule and persistent presence) are enforced. Systems will learn about the baseline attributes of each camera, including the approved field of view, areas of focus and other settings. AI modules will detect changes in these attributes and be able to identify if a camera has been knocked askew, critical areas are no longer in proper focus, home positions have been reset or other settings have been altered. Subtle performance degradations that may indicate the need for service or replacement will also be spotted well in advance of outright failures, thereby eliminating more costly and impactful downtimes.
Enhancing Zero Trust
For both moderate and high-security applications, zero trust principles and least privileged access will be further enhanced when AI-enabled security systems are integrated with operations and work authorization systems. Once systems are trained on facility attributes, access control zones and asset location data, enterprises will be better equipped to proactively eliminate access over-provisioning in favor of a just-in-time model.
Granting most privileged permissions for longer than is necessary to complete work assignments and authorizing access to areas unrelated to specific tasks will no longer be a default posture. The higher risks associated with blanket access will be materially reduced when security and operations work together to seamlessly enable permissions for only those locations requiring access to perform specific tasks. In addition, persistent access will be replaced by temporary permissions, whereby once a task is completed or the allocated time to complete work has expired, access will be automatically revoked.
Supercharged Investigations
Investigation teams can look forward to using natural language query features to produce more thorough and timely results. Machine learning modules will harness the power of AI to evaluate visual input from cameras and other sources. Classification, object detection and image analysis techniques will transform both the speed and quality of incident response and after-action reporting.
Natural language queries will facilitate exponentially easier searching for related prior incidents using targeted prompts. After a suspicious incident involving a person on a green motorcycle at the facility entrance, for example, an investigator could query the video system for every other instance in which a person riding a green motorcycle was observed near the facility entrance. If circumstances warrant, customized alerting criteria could be created to alert security in real time whenever a person on a green motorcycle approaches the site.
Trends in the types of incidents and their root causes will be more easily identified across sites and regions, yielding more actionable intelligence supported by historical data. For those who want to take a more proactive approach to identifying potential problems, AI-prompted near-miss analysis can help identify security issues and policy violations that did not lead directly to a security incident but could have, or flag actual incidents that, for whatever reason, may have gone unreported. By identifying and addressing potential security problems before they occur, enterprises will have more power than ever to influence user behavior and attention to security.
Responsible Use
Threats to critical infrastructure continue to increase in sophistication, capability and frequency. Physical security stakeholders must thoughtfully consider how they will leverage emerging AI capabilities in a responsible way to modernize and transform physical security programs to address their most critical risks.
Implementing AI technology with clear and tangible links to the threats facing an organization eliminates any perception that the time and resources dedicated to such efforts are contributing to ineffective security theater. In addition to the obvious systems and technology implications, owners must also predict the impacts these innovative technologies will have on people and processes. Education is an essential first step in transforming any physical security vision into reality.
Responsible use will be best demonstrated by understanding AI systems well enough to choose the best solutions that work with existing systems, improve security, fulfill due-care responsibilities and keep promises to customers.
Embracing Opportunities
The physical security industry is now embarking on a remarkable journey to recognize the extraordinary potential that AI represents. Using AI in a responsible way has the potential to help solve our most pressing security challenges while transforming the way we work to be more productive, innovative and secure.
Business-relevant AI can realize a quick return on investment, especially when the intelligence is applied to support high value use cases, including security. For enterprises large and small, cost-benefit calculations must include both the direct and indirect costs of the AI system, as well as the savings associated with more efficient operations, reduced downtime, reduced numbers of incidents and lower overall risks.
AI is also increasing excitement for work by reducing the number of mundane tasks and creating efficiencies that help staff be more productive and creative in their roles. These opportunities are timely, as physical security must evolve rapidly to keep up with the pace of innovation, a distributed workforce and shifting economic drivers. Physical security organizations innovating with AI amid these challenges are poised to emerge even stronger.
