Say Hello to Social Spaces

Social applications will transform the security experience

Steve Van Till. Brivo Systems
Social networks and social applications have become the single hottest growth category for both web and mobile technology. In hindsight, it appears to have been destiny.
It’s as if the cloud and mobile had a baby, and they called it social networking.
It has become not only the biggest growth category for new startups, it also represents the single largest technology IPO in the history of the U.S. stock market. Social applications have literally transformed the way our society uses computing devices, and they now account for the second-largest amount of time spent using mobile devices. Social applications have proven useful in fields as diverse as real estate, navigation, family management, reviews, business networking and news distribution.
And, yet, social applications are almost entirely absent from the world of commercial security. Why is that? Is it just because no one has made the connection?
Outside of the security industry, there is a growing trend called the “social Internet of things,” which is an offshoot of the better-known “Internet of things.” It describes physical devices that are connected to social applications so that we can interact with them in the same ways we interact with people. Status updates, texting, group updates, checking in, posting photos, all that, with so-called “social things.” A television, for example, may be connected to several social networking accounts and be able to tell people what was watched and when. Refrigerators, meanwhile, are now famously connected to social media and can take part in a dialogue with owners and the purveyors of their favorite products.
If these common consumer “things” can be social, why not the more industrial or commercial products we use to manage our physical infrastructure? What if the physical spaces we manage had the same ability to interact as consumer products when connected to “social devices”?
What if our buildings knew who we were and why we were there? What if public places could talk about their security concerns? How would that change the practice of security?
How would “social spaces,” to define a term, change the management of public places?
Even though the security industry is often late to the party for new technology adoption, it seems inevitable that social applications will find their way into the industry sometime soon. When they do, they have the potential to introduce some of the most sweeping changes we have seen since the introduction of IP technology. A few of the likely outcomes include:
- Enabling a more participatory security process
- Blending the security experience into business processes
- Improving real-time situational awareness
- Creating more intuitive and less obtrusive interactions
- Generating massive data sets about how our spaces are actually used
What Does It Mean to Be a Social Space?
Amid all of the discussions about “social networks” and “social media” and “social applications,” one rarely finds a definition of what it means to be social. We know that people are social. Animals certainly appear to be social. But can a building or a physical space be social?
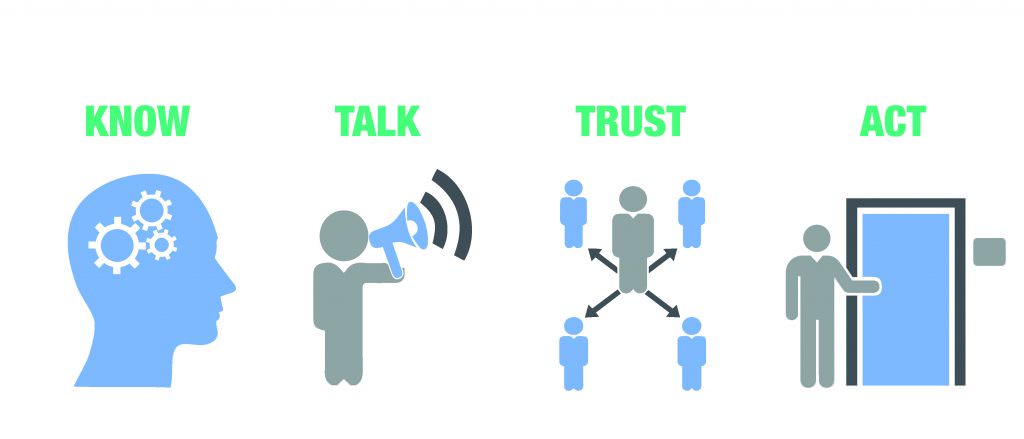
When it comes right down to it, being social is mostly about how something interacts with the rest of the world. For our purposes, we will just say that if something exhibits social behaviors, then it is social. To narrow that down a bit more, in this context, there are four key behaviors that are important for social spaces:
- They can know who you are
- They can talk to you
- They can learn trust
- They can take action
Know
Social spaces will be able to identify and know their inhabitants, visitors, guests, caretakers, administrators and any other people who interact with them. This knowledge is a fundamental building block because social relationships are built on the concept of a stable personal identity over time. This means that social spaces will need a way to identify people uniquely, in a way that does not randomly change, preferably with reference to an external identity provider. Social spaces will also need to understand the attributes and roles that are meaningful in the context of their interactions with us. The way we are greeted, where we are allowed to go, and whatever assistance we receive, for example, will all depend on who we are and why we are there.
Talk
Being social is all about communicating. No communication, no social relationships. Social spaces will communicate with us through social applications, just like our friends and colleagues do today. The more natural this communications is, the better. So instead of having to learn a new application for every place we go, it should be possible to communicate with a social space as if it were a person, using text or voice exchanges. You could ask a social building to let you in, lock the door, or perhaps allow a guest to visit on a particular date, all without having to learn a new application or switch out of the applications you’re already using.

Trust
Social relationships are based on trust, and trust is based on familiarity. That is why your dog barks at strangers and not at your friends. A social building wouldn’t bark at your friends, either. For social spaces, trust would be built up over time, the same as it is between people or animals. Frameworks to support this type of learned trust are a hot topic in identity research, and automating trust relationships is a thorny problem. That said, automated trust frameworks that operate in public spaces are an important tool for managing the growing number of security concerns we face. The sheer number makes it impossible to manage all of them through explicit rules, as we have in the past. At some point, our things and buildings and spaces will need the ability to operate more like we do, and learning trust is a big part of it. The social graphs embedded in social networks provide a rich data set that can be leveraged for this purpose.
Act
Ultimately, the whole point of creating social spaces is to empower them to take actions based on the ability to know, talk and trust. For example, a social space could remember its past interactions with a person and change its way of dealing with that person as it gets to know him or her better. A social building will know if someone is a friend of someone else and perhaps allow her to enter where a complete stranger would not be permitted without an escort.
It’s All About Identity
In order for social spaces to become a reality, they need to be able to identify people and share an identity of their own in return.

Today, we do not really have an agreed upon way in which to assert identity with any universality or uniqueness. The fact is, there are actually too many ways for us to identify ourselves, but they are all bound up in the small world of whichever organization issued us a particular identity token. When we go to work, we use an access card from our employer. When we go to the gym, we use a card from the health club. When we use an automated garage, we have yet another identity based on the fob assigned to our car. This means that we are always identifying ourselves as someone different when we go to different places. And none of these identities has anything to do with the others. No wonder our buildings don’t know who we are.
There have been many attempts to find an identity provider that everyone can agree upon, but, so far, none of them has really stuck. The security industry, for example, has many ways of identifying people, but each suffers from a lack of uniqueness and scope. People outside the industry are horrified to hear that proximity cards are not necessarily unique. Smart cards are helping, but the market has been slow to shift to the new technology.
The federal government has made several stabs at this as well, but the closest thing to a national identity initiative is the National Strategy for Trusted Identities in Cyberspace (NSTIC) program run by the National Institute of Standards and Technology (NIST). As a government initiative, however, it faces many adoption hurdles, especially in the wake of the controversy over the NSA’s domestic data collection.
In some sense, though, the public has already voted for its favorite identity providers, and they appear to be the social networking companies. Facebook likely has the largest user base using its credentials to register and log in to third-party websites. Google has been pushing its Google+ credentials for the same purpose. We are even seeing B2B companies like salesforce.com acting as identity providers for enterprise customers.
Against this backdrop, a social space still needs to have its own unique identity in order to interact with social applications on a social network. It is likely they will go in the same direction as the rest of us, using the available commercial identity providers that have become a common way of identifying ourselves online.
Social Communication Channels
One of the main benefits of having social spaces with social identities on the same network as the user community is that it would enable everyone to communicate with each other using identities and applications that are already part of their daily lives. These communications could be one-on-one, such as a request of or command to a social space, or they could be group messages, with a community of interest being privy to the same stream of information about a particular space or building. They might also be messages about special events, like the arrival of a guest or a change of venue.
We are seeing the emergence of this use of social communication for personal and neighborhood safety in, for example, certain applications that provide integrated messaging and location tools to members of a family. If someone fails to arrive at a location when expected, or goes somewhere he or she should not, geofencing algorithms trigger alerts that allow family members to respond.
Applying crowdsourcing to security is a very powerful way of thinking about how we can increase the benefits of electronic security in general.
Such tools could easily be applied to commercial and public spaces, where the space itself and everyone who uses it are part of the community of concern and are allowed to share relevant information across the social channel.
Security as a Customer Experience
It is probably fair to say that most of our encounters with building security are less than positive. One of my recent security experiences included a long wait in a lobby with a hostile guard who acted like everyone entering “his” building was lying to him about who they were and why they were there. Then there was a long wait while security tried to find the person I was there to see. Even in more hospitable lobbies, the best you will get is usually the stranger treatment involving impersonal processing and a cumbersome sign-in procedure.
The point is, when it is your building, everything about this user experience is turning off your customers. So what should customers expect? A customer experience, that’s what.
There was a great line from a Mad Men episode in which Roger Sterling, an advertising executive, reminded a colleague, “The client should never experience a negative emotion while in your presence.” That should also be true for people – customers – any time they are in a secured space.
A truly social space could be set up to know in advance who will be visiting. With that information, the guest could be welcomed by name upon arrival, rather than being treated like a stranger and handed a clipboard. By using a mobile credential or pass sent in advance, registration and badging could be as simple as scanning the invitation. The social space would then use a preferred social network to tell the hosts that their visitor has arrived. This would transform an impersonal security interaction into a welcoming customer experience.
Crowdsourced Security
Social spaces give rise to the possibility of what might be called “social security” – if the term were not already in use – or “crowdsourced security.” Crowdsourcing is the practice of obtaining services from a large group of people who are part of an online community, rather than a traditional employee responsible for that function. Applying this concept to security is a very powerful way of thinking about how we can increase the benefits of electronic security, in general.
Consider the usual model for intelligence collection and protection of a building. It is having one or more dedicated guards or other security personnel watching computer screens and cameras. This is an expensive process, and there is no way that a small group of people can ever hope to be as observant as a large group. And many companies, small businesses in particular, cannot afford to have dedicated security departments. But every company has an employee base that could be plugged into a social network group that receives alerts or images about possible issues.
Awareness is readily generated through crowdsourcing, and many of us are already using such crowdsourcing without knowing it by that name. It has become commonplace to look at online (crowdsourced) reviews of restaurants, hotels, vacation spots, mechanics and many other commercial services. This same socially sourced model fits with the trust level that might be associated with any particular individual entering a public space. Think of it as a personal review of every person who might be entering your building.
Forewarned is forearmed, and more awareness is always better.
When Is It Coming?
Social spaces are not exactly here yet, but many pieces of the puzzle are coming together:
- The use of mobile phones as an identity platform
- Wearable computing devices that interact with their environment
- The proliferation of application programming interfaces (API) for cloud-based social platforms
- The relative ease of stitching services together to form a social fabric around “things”
- The emergence of social applications that include interactions with inanimate objects like cars, refrigerators and other connected home appliances
- The growing acceptance of social applications in the business world
Like many other technologies, social computing will move into security slowly at first, then it will become pervasive, and, finally, it will leave us wondering how we ever did without it.
Steve Van Till is president and CEO of Brivo Systems (www.brivo.com) and vice-chairman of the SIA Board of Directors Executive Committee. He can be reached at steve.vantill@brivo.com.
