More than Just a Silver Lining

Using the cloud for access control enhances scalability, availability, resiliency, flexibility and security

Denis Hébert, Feenics
The power of the public cloud has become a catalyst for a dramatic shift in the information systems and security worlds. On-premises solutions no longer exist in many domains, from customer relationship management to expense management to human resources systems to learning management. For example, more than 50 percent of enterprise resource planning installations are now being deployed as cloud-based services.
This phenomenon is the result of the substantial benefits afforded by cloud-based systems, such as scalability, availability, resiliency, true flexibility and strong security – all of which add up to a lower total cost of ownership. At the same time, this phenomenon has spawned the era of “as-a-service” business models, providing subscription-based alternatives to the traditional capital-intensive approach of business applications. As indicated in the accompanying diagram, the real cost of ownership for on-premises solutions is often not considered.
The security industry is not immune from this trend; in fact, it has been rather intimidated by it.
Yet, interest in and adoption of cloud solutions has slowly started to happen, and it will eventually become the norm rather than the exception, especially as end users become more aware of what flexibility in the cloud means when it comes to physical security.
It should be noted that true cloud solutions do not simply mean the virtualization of the standard client/server architecture “parked” in someone else’s data center and referring to itself as the cloud.
True cloud-based applications are designed from the ground up as a cloud service and are hosted in a proven, secure public cloud infrastructure.
This is an important distinction, as the only way to truly leverage the comprehensive benefits of a cloud service is to design for a cloud service from the very beginning.
Scalability
The traditional model of on-premises access control applications has been limited (at times artificially) to door counts or blocks (e.g., 32/64/128/256), labeling versions as lite, enterprise and so on. In most cases, this means greater hardware requirements for running the system, and if globalized for enterprise environments, it requires supplementary hardware to manage regions. For smaller systems, this implies onerous expenses for hardware, which is conceivably over-the-top and does not match the actual need. The more doors added as a system grows, the greater the hardware requirements to manage the data, polling, synchronization, reporting, operating locations and other core functionalities. Either way, organizations find themselves in the computer hardware management business.
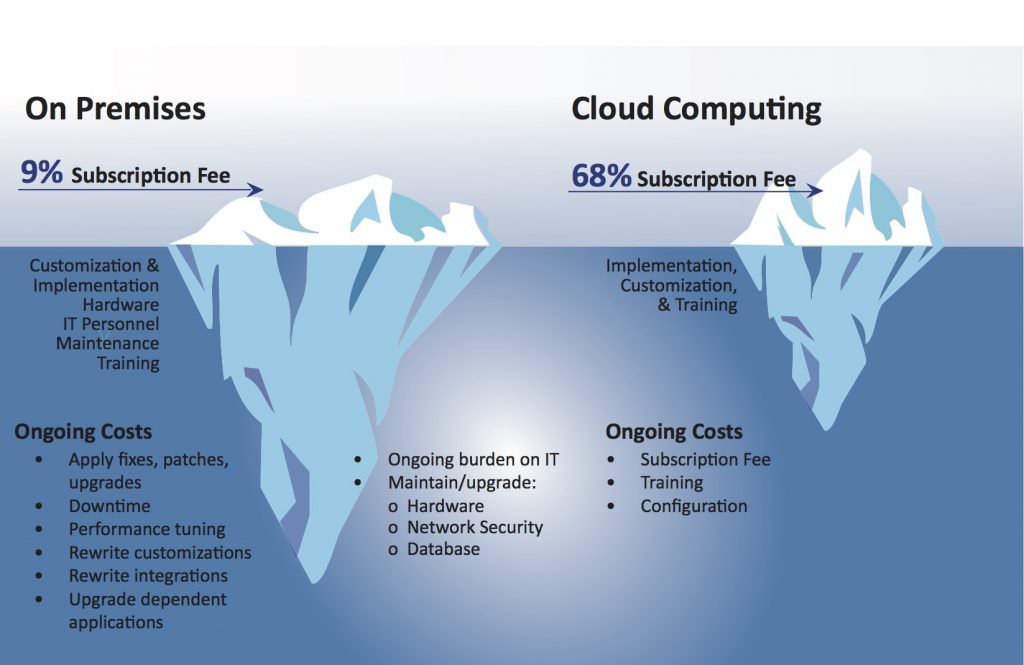
Public cloud-based applications alter the scalability landscape. System size – and the ensuing scale required to manage it – becomes a function of subscription count; in other words, it is tied to usage. This elasticity of expense goes up and down easily, transparently and seamlessly. Orders of magnitude become irrelevant since the cloud absorbs load based on its horizontal scalability and load balancing. When it comes to access control, this means that organizations can increase or reduce the number of doors or users without experiencing delays or bear unnecessary costs. This on-demand scalability provides added flexibility and greater agility to easily respond to evolving security and business requirements.
Availability
The key to security has always been system uptime. This applies to intrusion, video, fire and access control, and it is accomplished either at the field level with battery backup or at the host level with costly “hot” systems. Even with this expense, activities related to patching or version control inherently require some downtime, thereby affecting the availability of a host. This does not include power outages, polling device inconsistencies and other impacts to availability.
Public cloud-based applications bring 99.999 percent availability characteristics, resulting from the capability of the provider to upgrade, patch, change versions and make any other modifications without affecting customers.

Accomplished with complete transparency to users, there is no impact on service levels, beyond a client’s ability to connect to the Internet.
Resiliency
Though related to availability, the key element to consider when assessing resiliency is the concept of failover caused by an uncontrolled event. Most on-premises applications do not provide for this, as it is cost prohibitive to do so. Resiliency can only be addressed through hot or cold standby, redundant array of independent discs (RAID) technology or other mechanisms, which, if done, are likely implemented in the same location or nearby. This does not address the problem of a major uncontrolled event such as a flood or earthquake.
Public cloud-based applications can address the resiliency issue by leveraging their design, which is based on geographically-distinct availability zones. Services that cannot be provided in a given geographic location or zone because of a disaster are automatically handled in a different location or zone in a fashion transparent to the user. This redundancy provides the user with an important benefit without requiring additional hardware and expense.
Flexibility
Physical access control systems have traditionally been developed and designed to be somewhat static in their approach (e.g., door definitions, access rights, cardholders, schedules). The databases derived from these attributes and the ensuing events become an integral part of the access control solution, whose purpose is to then systematically create audit logs and reports. That said, the data becomes the property of the access control system. In this scenario, an end user’s desire to interact with the data is limited to the functionalities provided by the manufacturer’s interface.
This leads to the question, “To whom does the data belong?” If the dataset is created by an end user, for the end user, then it should belong to that end user to work with as they see fit. Open database connectivity (ODBC) connections are too limiting in their capability for true data management and are, therefore, not the method of choice for large datasets in the cloud.

Effective data management is accomplished using real-world tools that empower the data owner to interact fully with the dataset. In today’s world of big data, this implies the use of application programming interfaces (APIs). Cloud-based systems designed to use a single API provide this approach, as well as the associated tools needed to interact with the data. A resilient API provides the access control service provider a point for its user interface to work with, as well as all associated services – including communications, database, and applications. In addition, such an interface enables the script to have customized requirements for interacting with the data (for example, adding metadata, changing parameters, adding and changing data, creating data-specific reports – all without compromising the integrity of logs and transactions). An API-centric architecture enables the agility to build flexible, fully scalable applications that can be easily connected to other systems inside and outside the enterprise while being future-proofed to accommodate new technologies.
Security
The idea of housing an access control system on premises to ensure the highest level of security is a thing of the past. The question one should ask today is, “What level of security do we practice internally, and how is the manufacturer ensuring the security of their application?” The likelihood of these questions being answered favorably is questionable at best. Enterprise security is often a struggle for the best IT departments, primarily because of staffing demands and the expense of keeping systems updated. This is provided that the on-premises system is actually managed by the IT department, rather than the security operations center.

The second part of the question is especially difficult since most access control manufacturers do not have a robust (if any) methodology for testing the vulnerabilities of their applications. Conversely, cloud service providers depend on the security of their service for business survival. Constant threat monitoring and vulnerability scanning are key to their existence. Therefore, the hardware and resources dedicated to security and data privacy far outweigh those in the majority of businesses today. The resources dedicated to security, compared to a typical organization, are incomparable.
Application security is an area of even greater concern. It has not been a best practice in the physical access control world to consider the potential vulnerability of applications. In fact, very few systems providers would even comply if end users were to make application security a core requirement. Yet, the security industry is responsible for providing the most secure solutions possible.
The industry should mandate, as a best practice and built-in specification, continuous vulnerability scanning of all applications and physical access control systems.
Summary
Increased scalability, availability, resiliency, flexibility and security are all part of the affordable, realistic benefits of a public cloud infrastructure. Cloud solutions help reduce the initial capital investment by eliminating the need to purchase costly software, while also reducing the staff and training required to maintain the system, leading to an overall decrease in the total cost of ownership. By moving infrastructure to a cloud-based model, organizations can focus resources where they belong: on developing innovative solutions that grow their business. The time and money spent making technology decisions for access control, along with hiring staff to manage and maintain the infrastructure, can be a thing of the past.
Denis Hébert (denis.hebert@feenics.com) is president of Feenics (www.feenics.com) and is
chairman of the Security Industry Association Board of Directors.
