How IoT Allows for Physical Access Integration into 6 Layers of IT Systems

 Physical security and IT systems are better together—as explored in this post. But until recently, a specific concept on how to approach the obvious on a technical level was missing. In this blog, we explore the concept of physical security running like an app on the IT infrastructure and what that would mean in terms of integration.
Physical security and IT systems are better together—as explored in this post. But until recently, a specific concept on how to approach the obvious on a technical level was missing. In this blog, we explore the concept of physical security running like an app on the IT infrastructure and what that would mean in terms of integration.
Why IT and Physical Access Control Systems (PACS)?
Too long physical security has been treated itself as something out of the ordinary—IT that requires special assistance by vendors to help maintain and operate its functions. No other category in IT systems has itself withdrawn so much from progress like physical security. Today companies can manage entire data centers with a Software as a service (SaaS) dashboard, but often they still have dedicated (unpatched) PCs in their server room to program cards.
Until recently, that was okay and accepted as common practice. However, not only is the nature of work changing but also the workplace itself: With the distributed workforce, facilities experience higher turnaround, volatility in workforce and external vendors than ever before, and it is steadily increasing. Corporations don't rely on one big headquarters but have a large amount of distributed facilities across the nation or even the world.
The Internet of Things (IoT) Is About to Run the Office
At the same time, industrial IoT starts to reach into the physical office environment with the goal to transform the office into a big computer. This IT vision preaches that each device should be remotely managed and integrated into enrollment processes. IoT becomes a synonym for the place where the digital world meets physical reality.
Making the physical world controllable with IT tools provides the chance to roll out IT's operations standard in terms of security, capability and user experience across physical infrastructure in the office, which happens to include doors. Access control as a service is emerging as serious industry category expected to growth 26 percent per year (Source: marketsandmarkets.com). Early adopters are modern IT departments who run their stack on a cloud-based SaaS stack.
The Access-as-a-Service Stack
While this all seems like a nice vision, we've looked at the PACS stack and tried to showcase how the PACS parts in each layer could ideally interface with IT systems. If done correctly this would make the PACS system a fully operated and automated IT SaaS system. Here is an overview of the 6 layers we found to be connecting with IT:
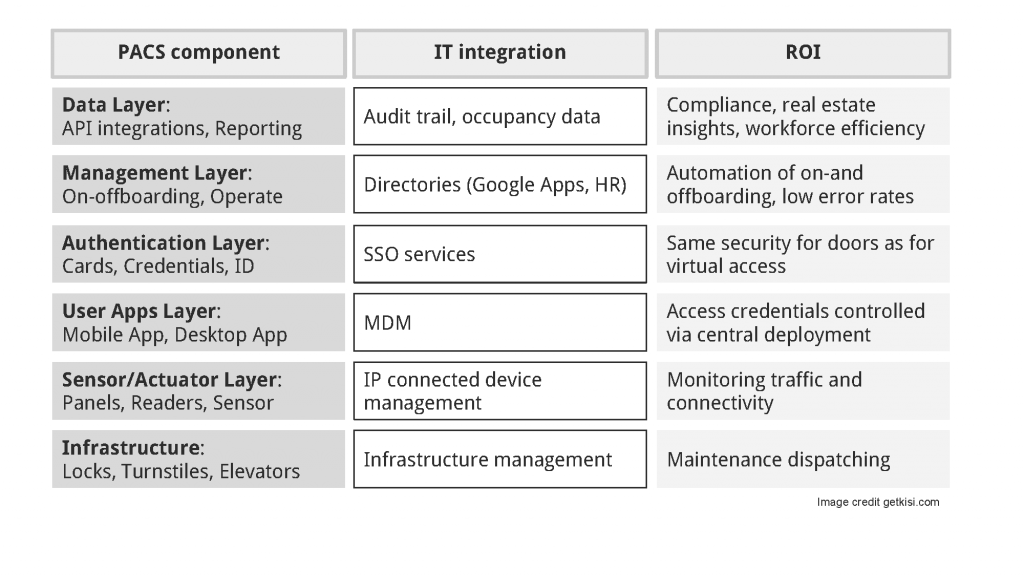
1. Infrastructure locks layer
As part of the infrastructure layer, locks and other electronic access points need to function. It is critical to monitor their ability to operate similar to internet availability or power supply at the facility. Common IT requirements are hot standby system failover functionality. IT facilities management includes all aspects of managing the physical environment—for example, power and cooling, building access management, and environmental monitoring. Facilities management and IT operations are growing together (Source: facilitiesnet).
2. Sensor and actuator layer
On the sensor and actuator layer IP connected devices like access control panels, door contact sensors or proximity reader management allows to block or specifically allow data traffic to flow through. Typically, access point management software and firewalls, as well as certificate management in larger organizations, are part of this IT strategy.
3. Device layer
Using mobile device management (MDM), IT managers control the device layer. Making sure software is up to date on every active device, controlling apps running on them and securing their connections are main priorities. This is one big reason why the main access method in the future can't be keycards, because they can't be controlled nor integrated into MDM environments.
4. Identity layer
Identities are managed in the user-credential layer with the help of Single sign-On services. Any authentication against a device should happen through a verified, secured and controlled identity that is managed by IT.
5. Management operations layer
On- and off-boarding employees through the management operations layer is coordinated through directory services who are the source of through of who is allowed for which level of permissions.
6. Data layer
Integrating different systems via the data layer is achieved through out-of-the-box integrations or manual API integrations, allowing for centralized audit trails to create compliance or occupancy data to manage facilities insights and workforce productivity.
Looking Forward
The future of physical security lies in its cybercapabilities. The profile of an access control manager will merge into a form of IT systems engineer who runs critical infrastructure systems—among others: doors.
For more information about KISI, visit www.getkisi.com.
The views and opinions expressed in guest posts and/or profiles are those of the authors or sources and do not necessarily reflect the official policy or position of the Security Industry Association (SIA).
