Everything Changes: Integrating Mobile Credential With Push Notification
In 2018, what is one of the technologies in our industry that is ripe for “game change”? Where will we see the rules of the game change forever in access control and how? In a word: Credentials.
Why do we make this claim? Three main reasons:
- Smartphone-based credentials are inherently more secure.
- Smartphone-based credentials can do so much more.
- Smartphone-based implementation can significantly reduce installation costs.
Welcome to Mobile Credential 2.0.
Your Biggest Security Risk
Forget about high-security credentials such as mifare and sophisticated certificate handshakes. The single largest security risk with access control is a valid credential in the wrong hands. When that happens, it doesn’t matter if it’s a 125KHz “dumb” prox card or the most sophisticated smart card; a potentially malicious user now has access, and no one will know if that lost or stolen card isn’t reported.
Your smartphone as your credential is significantly more secure because of one simple fact: People don’t necessarily know the location of their access control credential at any given time, but they are intimately aware of the location of their smartphone at all times. They are naturally much more careful as to whom they allow to hold or use their phone.
A large manufacturing end user once estimated that approximately 30 percent of employees were entering the grounds without their credential at any one time. The user would wave something that looks like a credential at the guard shack and yell that it didn’t work. With 600 people coming into a shift change and cars backing up at the gate, the guard would open the gate to keep traffic flowing. That’s a solution?
The Power of Mobile Credentials
So, how is the world of credentials changing forever? A smartphone-based credential can be so much more, do so much more. In the near future, we’ll start to see features such as:
Multifactor authentication (MFA). Smartphones already implement MFA. Soon, new mobile credential implementations will allow administrators to require a screen unlock pin/biometric/gesture to set up a mobile credential, thus implementing MFA with no new hardware at the door.
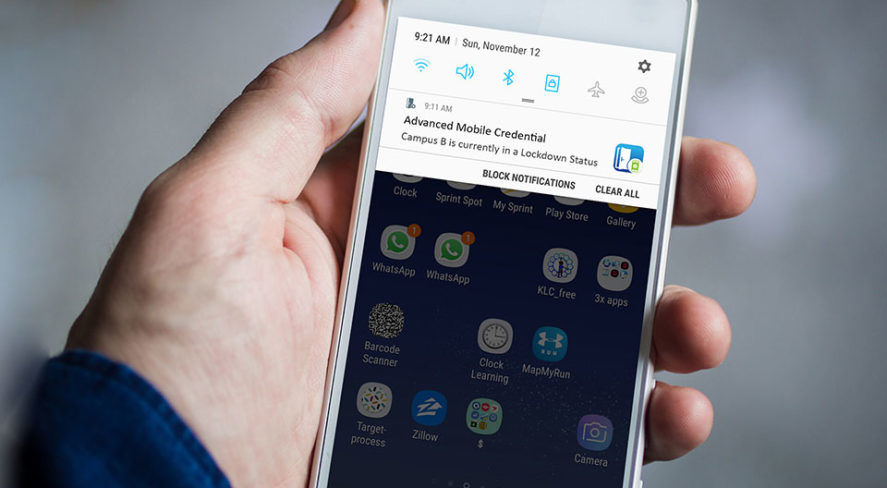
Mass notification. A credential—supporting two-way communication with active notification capabilities—can be leveraged to send automated or ad-hoc notifications to users. Add location services, and you can send notifications only to those who are within a specific geographic area. And you can target those notifications to specific people.
Location awareness. Stop treating a smartphone like a legacy credential; no one should ever “badge” a phone at a reader. By using location services, administrators will define how near the door a person must be to request access.
Virtual buttons. With an app for users that uniquely identifies them, why not give them more? We’ll see the ability to add virtual buttons to an app to perform functionality specified by the administrator—and only distributed to those allowed to use them.
Revoking a credential. An administrator can disable a user’s mobile credential at any time from the server with no need to access the actual smartphone. The smartphone app knows how to submit a credential request but has no idea how to unlock a door, only the server can do that. Additionally, administrators can remotely wipe users’ smartphones of the mobile credential and related apps connected to the corporate network.
More Features, Low Costs
Finally, let’s consider cost. A smartphone credential will add significant functionality over a traditional credential and be upgradeable to add new capabilities—all for the same cost, or less, as that of traditional credentials. Also, users do not require a reader to enter a door, so enterprises can eliminate readers on most doors to keep the entrance clean and to reduce installation costs.
Over the next 24 months, we will witness unprecedented change in the tools and services you use every day, and one of those tools will be your access control credential. The security of a door is only as strong as the management of the credential. It only makes sense for that critical credential to be secured inside the most highly encrypted device—your own smartphone.
The views and opinions expressed in guest posts and/or profiles are those of the authors or sources and do not necessarily reflect the official policy or position of the Security Industry Association (SIA).
