Intelligence Cycle: Tips and Tricks

Risk monitoring, brand management, executive protection, crisis events, and more all depend on effective intel—uncertainty paralyzes action. Having the right intelligence, in real-time, is critical to mitigating risk and protecting your assets. Corporate security professionals can gain vast amounts of intel by gathering results from location-based intelligence.
This three-part blog series will explore how organizations can leverage the Intelligence Cycle to predict, analyze, and act on location based intelligence. Then, we will demonstrate how corporate security organizations can power their intelligence cycle with social data using a location-based platform.
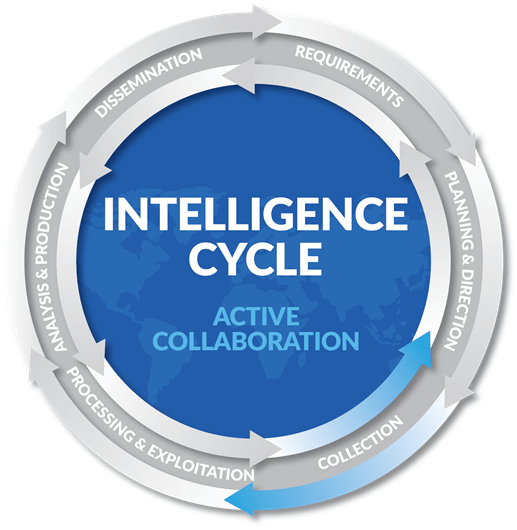
The Intelligence Cycle is a six-step framework that guides data operations in organizations of any size or complexity. These six steps to outline a measurable and repeatable framework that helps organizations like yours make data-informed decisions:
- Requirements: Identify what information or what kind of data defines an event. This step is critical—without proper definition finding actionable intelligence is nearly impossible.
- Planning & Direction: Decide your strategy. Create an outline discussing which sources matter and how to collect viable data. An effective data collection plan is based off of your already defined requirements.
- Collection: Data collection comes from a variety of activities, such as surveillance, interviewing, social media monitoring, and personal operations. Utilize a location-based intelligence platform to collect real-time, specific data from a multitude of social media sources.
- Processing & Exploitation: Raw data is messy. Before you can analyze the data you’ve gathered, it needs to be readable by analysts. This could include decryption, translation, standardization, and many more data cleansing methods. This process generates usable inputs for analysts to interpret and apply to other components in your organization.
- Analysis & Production: Here, your data turns into real intelligence. Produce insights that inform your organization’s security operations. Analyze the sources you’ve processed to validate reliability, link previously undiscovered connections, and find new forms of intel.
- Dissemination: The urgency and format your collected intelligence all depend on the nature of the data you have collected. On major unexpected events, the intelligence dissemination may take the form of an instant phone notification to potentially affected individuals, while a full security audit may take the form of a yearly report. This is a critical point of the intelligence cycle—effective action depends upon effective intel dissemination.
With every cycle, it is important to take a critical look at what went well, what did not go well, and how your organization can improve your processes. Understand new ways to predict, analyze, and act on advanced intelligence.
As a security professional, the Intelligence Cycle organizes your surveillance process into a repeatable and scalable framework. Geofeedia shortens the intelligence cycle by combining every step into one easy-to-use platform.
It isn’t hard to imagine your executives traveling daily to destinations all over the world. See five ways the intelligence cycle is applied to enhance security operations in the next post: “5 Ways Location-Based Intelligence Aids Security Risk Mitigation.”
For more info on “Mastering the Intelligence Cycle,” obtain your copy of a Geofeedia white paper on the topic here.
The views and opinions expressed in guest posts and/or profiles are those of the authors or sources and do not necessarily reflect the official policy or position of the Security Industry Association (SIA).
