How the Security Industry Handles Cybersecurity

We asked you what steps you were taking to ensure the cybersecurity of your physical security systems. The results were eye opening.
To better understand how the industry is approaching cybersecurity, we decided to ask the industry.
What we wanted to know was what specific steps companies were taking to secure the systems they installed. Were they changing default passwords? Were they hiring penetration testers? Were they disclosing known vulnerabilities?
What we found was a tale of two extremes. Some respondents approached cybersecurity of physical security systems like video surveillance and access control very seriously, but we also saw some significant cybersecurity gaps from respondents.
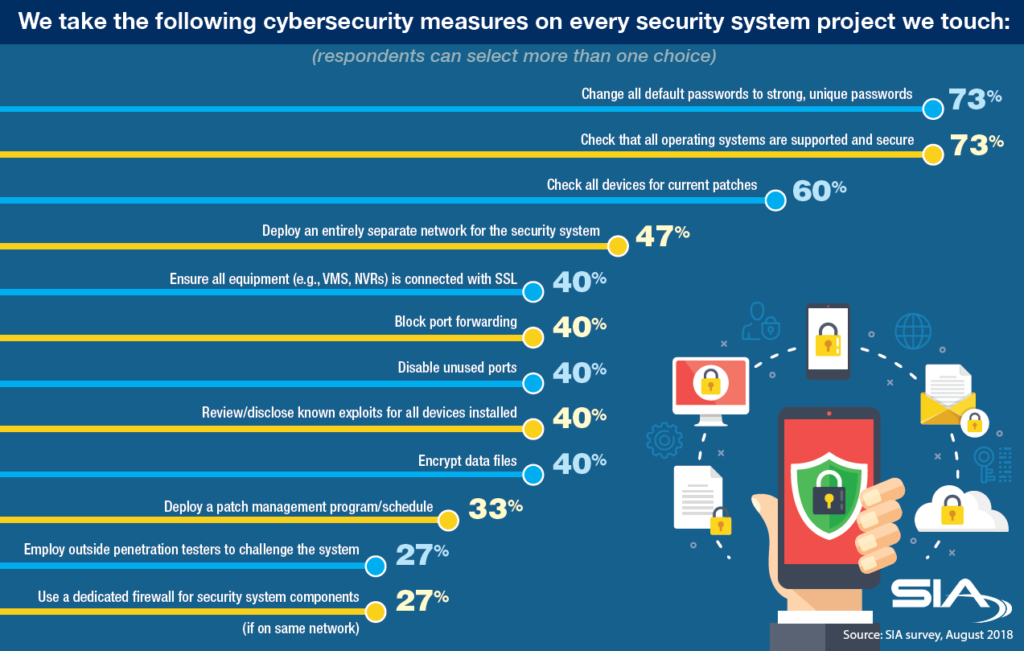
On one hand, 27 percent of respondents said they use a dedicated firewall for security systems components if those components were running on the company’s main business network. Some 27 percent also said they were hiring outside penetration testers to challenge their systems – whether this was being done after install or during system and product design phase was not asked. In general, this was very good news. We did not expect that the use of penetration testing would be this high.
But on the other hand, there was still a lack of basic cybersecurity practices by some companies. Only 73 percent were changing all default passwords to strong unique passwords. This percent is quite simply concerning. When security systems are left with default passwords, they might as well have no password – as the default admin passwords are well known and posted all over the internet. No number of patches or other steps can supplant the fact that a malicious actor could log into the system directly with a default password.
We also found that only 73 percent were checking that all operating systems were supported and secured, and only 60 percent were checking for patches and updates. These are potential blind spots in terms of cybersecurity, and leaving devices unpatched, not updated and using out-of-date operating systems all means more potential cyber weaknesses.
What’s more, only 40 percent of the respondents said they review/disclose known exploits for all devices installed. On this, we recognize the innate hesitancy to tell a client that their new security system has known vulnerabilities, but before we consider that the final decision, let’s not forget about issues of liability and of the need for a chain of trust between the client and their supplier. If clients are empowered with knowledge, rather than kept in the dark about known vulnerabilities, we believe this open communication develops the needed trust that should exist between the customer and you, their chosen security advisor. Further, many security researchers are actively looking to report vulnerabilities to vendors, and often only “leak” bugs to the media if they have been repeatedly ignored.
Other findings:
- 47 percent deploy an entirely separate network for the security system
- 50 percent ensure all equipment (e.g., VMS, NVRs) is connected via SSL
- 40 percent block port forwarding
- 40 percent disable unused ports
- 40 percent encrypt data files
- 33 percent deploy a patch management program/schedule
Kudos to the respondents practicing the above, but as an industry we need to see those numbers tick upward.
In conclusion, while there are bright spots in the data, the overall perspective following this quick survey is that the survey results should serve as rallying call for the industry to take cybersecurity even more seriously. Some recent SIA resources to help you down this path include:
- Cyber:Secured Forum (July 29-31, 2019) – a conference on how to increase the cybersecurity of physical security systems
- The Cybersecurity Imperative – a study of cybersecurity best practices of global businesses, creating benchmarks your own firm can follow
- SIA Cyber Office Hours – a regular webinar-style program which allows direct engagement with a SIA cybersecurity expert to answer your cyber questions, and it’s free for members
- Cyber Onboarding Guide – a quick-read document to help make new employees cyber aware
- SIA Cybersecurity Advisory Board Enterprise Security Recommendations – general recommendations for initiating a culture of corporate cyber-awareness and responsibility.
Every other month, SIA produces the Security Market Index, a members-only publication that analyzes market and business growth confidence. In each issue, the report also surveys the SIA membership on a topic of high relevance; the September 2018 edition of Security Market Index focused on these cybersecurity implementation topics.
